Hey everyone,
To make our featured challenges more exciting, we are going to award Limited Time Badges to those that complete the Challenges in time.
For the 2nd half of September, we will be putting the spotlight on: Confusable
You can go and try out this challenge at the Featured Game, completing all the challenges will award you a badge to commemorate your achievement.
This is a Limited Time Event that ends on 30th September
Introduction
URL spoofing is a deception tactic adversaries use to trick users into willingly exposing their personal details. This technique consists of the attacker crafting a URL that closely resembles a legitimate one, baiting susceptible users into visiting a fraudulent website.
(See Nord VPN’s blog for URL Spoofing)
Homograph attacks are a more sophisticated form of URL Spoofing, they exploit both system vulnerabilities and human psychology to achieve their deceit. This post aims to delve into Homograph attacks, with a spotlight on the notorious PayPal homograph attack as a case study.
(See Nord VPN’s Glossary for Homograph Attacks)
Anatomy of the Homograph Attack
Structure of the Attack
The core of a homograph attack lies in deception, specifically in the use of URLs that are visually similar to those of legitimate websites.
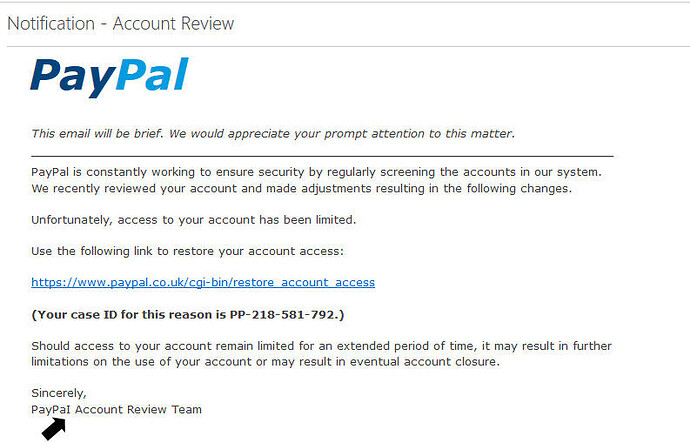
In July 2000, PayPal experienced a homograph attack that tricked some of its 2.6 million users into revealing their login credentials. Users received an email claiming they would receive a bonus in their PayPal account. The email directed them to PayPaI.com, which is actually paypai in lowercase, where they were prompted to enter their PayPal username and password.
Image source: dragonrider.co.uk
Because of the striking resemblance between the URLs and website designs as well as the clever use of capitalization, many users didn’t recognize the scam, making them vulnerable to potential financial loss and identity theft. Users were often lured into this trap via phishing emails, which appeared to be sent from PayPal itself, claiming that a bonus would be added to their account if they followed the embedded link.
(Read more about this scam at Seclists)
Manipulation of Human Psychology and System Flaws
These types of attacks exploit human psychology by relying on the idea that people trust familiar names and appearances. This is why a slight change in the URL, often overlooked by a quick glance, is so effective. Moreover, the use of capital “I” instead of a lowercase “L” is a system flaw that many might not notice unless paying close attention.
(You can learn more about this flaw in our free Visual Spoofing course on Learn)
Systems also tend to default to displaying URLs in a manner that hides their true nature. This is particularly true for IDN homograph attacks, where different character sets are used to make the URLs look alike. Therefore, users can’t rely solely on system-level security to alert them to these discrepancies.
(Read more about IDN homograph attacks at zvelo)
The targets in these kinds of attacks are often average, everyday internet users, but they can also include small-to-medium businesses and even large corporations. These targets are often chosen due to their perceived vulnerability and the potential for financial gain from the compromised accounts.
The Impact
While the attack targeted and affected individuals, it also undermined the trust and security of PayPal as a platform. Something that is foundational for online financial transactions. As the technology that supports these scams becomes more sophisticated, the risks only increase.
A 2006 study measured Homograph Attacks, while uncommon, the study noted it could be a potential emerging avenue for scammers.
(Read more about this in their Research Paper)
Relation to the Challenge
The Confusable challenge, which is the subject of our Featured Game, is built off the back of the PayPal Homograph Attacks. Effectively patching it across multiple languages will demonstrate your ability and understanding of the vulnerability.